Q2 2025 Cyber Incident Report


Key takeaways
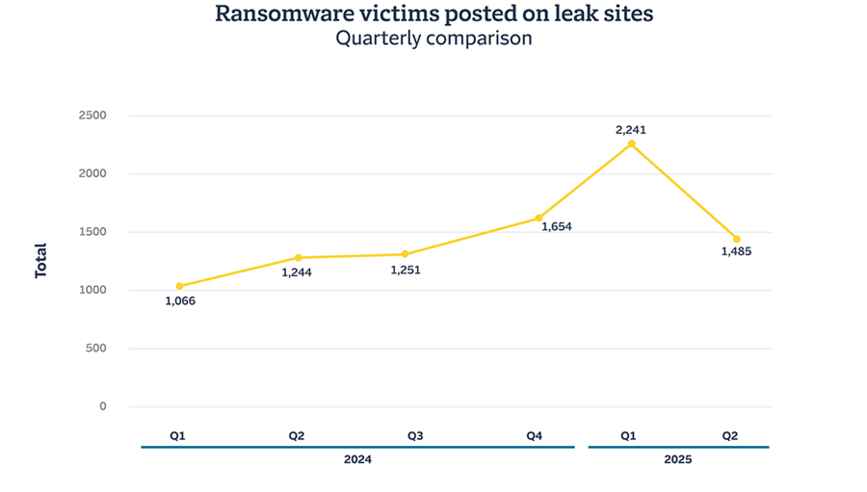
- Ransomware activity eases: Leak site listings declined to 1,485 incidents in Q2 2025, after reaching 2,241 incidents in Q1.
- Social Engineering Fraud and Business Email Compromise (BEC) continue to drive claims: When combined, these often-overlapping categories are consistently among the top three drivers of claims at Travelers. BEC exploits are evolving to include new tactics, including extortion.
How business email compromise and social engineering drives cyber claims
In Q2 2025 activity on ransomware leak sites, our proxy for overall ransomware activity, dialled back slightly – down to levels that put it in line with the long-term rise in activity observed over the past few years. That’s not overwhelmingly great news, but it’s far better than one possible alternative: that the elevated levels of activity observed in Q1 were only the beginning of an upward change in the trajectory of ransomware activity. It seems, for now, that is not the case.
The ransomware ecosystem is in disarray after law enforcement actions and internal strife led to the dissolution of notable groups of threat actors in the first half of 2025. We cover these happenings in this edition of the Cyber Threat Report, as we always do. But we’re also taking some time to focus on a less dramatic – but more consistent – factor in the realm of cyber threats: business email compromise (BEC).
At Travelers, situations involving BEC or social engineering fraud (a frequent outcome of BEC) represented nearly half of all cyber claims in the past five years. Clearly, this area of cyber risk is meaningful – yet it consumes a fraction of the attention that software vulnerabilities and ransomware do. We’re hoping to change that, just a tiny bit, this quarter.
Ransomware leak site activity declines Quarter-over-Quarter; Remains elevated against long-term averages
After reaching 2,241 incidents posted on ransomware leak sites in Q1 2025 — the highest quarterly total that Travelers has reported in four years of tracking this metric — listings declined to 1,485 incidents in Q2 2025. While any decrease in ransomware activity is notable, the activity in Q2 2025 is in line with the general upward trajectory in activity that began in Q1 2024 (at which time there were 1,066 incidents).
Contributing factors to ransomware activity in Q2 2025
Several factors appear to have contributed to the quarter-over-quarter reduction in ransomware activity. First, there has been significant upheaval within the ransomware criminal ecosystem over the past year. Early in the quarter, a well-known ransomware group called RansomHub suddenly went offline. RansomHub's affiliates were thrust into confusion when their negotiation platforms became inaccessible. Subsequent investigations by threat intelligence firms revealed that the group's administrators were dealing with disagreements with an unknown number of affiliates.
While affiliates working with RansomHub ultimately moved to other groups, this took some time. Meanwhile, several other groups took advantage of the void left by RansomHub, including Qilin, Akira and Dragonforce, the last group being a newcomer in Q2.
Another factor likely contributing to the decreased leak site activity was the takedown of LummaStealer, a popular type of malware used to gain initial access to networks. The takedown came on the heels of RansomHub’s strife and resulted in the seizure of over 2,000 domains in May 2025. Given LummaStealer’s widespread use by cyber criminals, this takedown likely interrupted a number of attempts at gaining initial access to victim systems.
While we can’t precisely determine the impact of these disruptive events in Q2 2025, we can surmise that many threat actors were forced to quickly adapt their approach to gaining initial access to victims and carrying out extortion threats, and this likely degraded their ability to carry out attacks during the quarter.
Looking forward: Long-term trends remain in place
While the quarter-over-quarter decline in ransomware incidents in Q2 2025 is a positive signal, we caution against any organisation relaxing their approach to risk mitigation. It's worth noting that the heightened Q1 2025 numbers may prove to be an outlier, with the number of Q2 2025 incidents continuing to follow the upward trendline we've documented since Q1 2021 when we began gathering this data. Ransomware remains a viable threat vector.
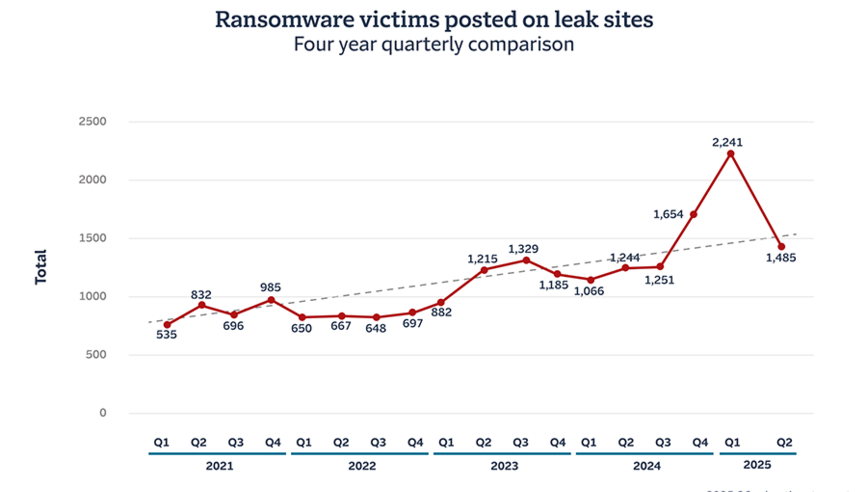
When taking a longer view of the data, what is clear is a consistent rise in activity from leak site data over time. This suggests that while law enforcement actions and improvements to cybersecurity controls can have a real impact on limiting the growth rate of the ransomware ecosystem, and even reduce activity in the short term, when we project across years rather than quarters our assumption remains that activity will continue to grow.
Social engineering and business email compromise: Key drivers behind cyber crime
As we reviewed in the previous section, the level of ransomware activity has a propensity to ebb and flow from quarter to quarter. Meanwhile, the threats of Social Engineering and BEC represent a quieter, but also more consistent threat – and one that has equally real financial consequences. In this section we’ll cover the basics of BEC, how it impacts organisations, and a couple of the ways that Travelers has observed BEC tactics evolving in recent months. We’ll also share some of the guidance we provide policyholders around security and operational controls to help defend against BEC.
Business email compromise: A primer
BEC describes situations in which attackers impersonate executives, vendors or individual employees after compromising a worker’s business account (often, but not always, an email account). These attacks frequently begin with a social engineering exploit, as attackers use phishing or spear phishing to gain access to the business account by tricking a victim into downloading malware, or by stealing their credentials through an adversary-in-the-middle attack (AiTM).
What makes a BEC situation distinct from a garden-variety phishing exploit is that the social engineering efforts don’t end with malware being deployed: they continue, only made more realistic and devious by the attacker’s ability to review internal company files and communications. In some cases, the attacker may send messages directly through the compromised account to instruct someone to send money to an account under their control; in others, they will use the intelligence gained by reviewing past communications to develop a realistic spoof of a partner or vendor account to achieve the same result.
Through this highly informed and highly targeted style of social engineering, attackers are able to trick employees into transferring company funds to the attackers. Over the past two years, Irish small and medium enterprises (SMEs) have lost more than €17 million to email-related scams, highlighting the significant financial risk posed to Irish businesses.
The cost of cyber fraud
Historically, BEC has not set off industry-wide alarms, as often happens when a ransomware group targets a string of similar businesses. While we’re starting to see more exceptions to this rule – as we’ll discuss below regarding the Scattered Spider group – these are attacks that don't feature the spectacle of encrypted networks and ransom demands. As a result, they are less widely reported and less discussed in business media relative to ransomware.
Yet according to the FBI’s Internet Crime Complaint Center (IC3), U.S. businesses reported more than €2.3 billion in losses from BEC scams in 2024. The FBI also found that over the past decade, global reported losses from BEC have exceeded €43 billion, making it one of the most financially damaging forms of cybercrime.
The two related claim categories, BEC and social engineering fraud (a frequent outcome of a successful BEC attack), combine to be consistently in the top three types of claims at Travelers and represent roughly half of all cyber claims in the past five years. Third party sources, like the Verizon Business 2025 Data Breach Investigations Report, also report consistent numbers of incidents from year to year – around 19,000 per year in recent years, with a median loss of €42,000.
At baseline, BEC is already a large component of the overall cyber threat landscape. But the style and tactics of social engineering and BEC are evolving and being used in new ways.
Tactics converge: Social engineering meets extortion
As we noted in our last two quarterly reports (Q1 2025 and Q4 2024), the “classic” ransomware strategy of exploiting software vulnerabilities has been on the decline. Our team has found that years of increasing ransomware activity has led to more widespread implementation of security controls and improved patch management practices by organisations of all shapes and sizes, making most software vulnerabilities less-effective targets.
With a few exceptions, such as the Cl0p group’s rash of attacks in early 2025 that targeted a software vulnerability, most of the currently active ransomware groups have been looking to other opportunities to gain initial access, like brute-forcing passwords. Another emerging trend in this category is threat actors leveraging the kind of sophisticated social engineering tactics often seen in cases of BEC, like those described above, but combining them with extortion. This combined approach isn’t entirely new, but it’s now being deployed as a central pillar of some groups’ strategies in a way that represents a break from the past.
Scattered spider: A case study in modern social engineering
A prominent example of a group combining social engineering, extortion and other tactics in a single attack is Scattered Spider, a loosely affiliated threat group believed to include members in both the U.S. and U.K. Known for its social engineering expertise, the group has been linked to several high-profile breaches, including incidents involving leading retailers and airlines in the U.K. and Australia. These attacks combined elements of BEC and social engineering, such as impersonating company employees to gain unauthorized access to internal systems, but the results of these efforts have gone far beyond the typical fraudulent transfers of funds.
In one of the more costly events, attackers tied to Scattered Spider used social engineering tactics to deceive IT helpdesk employees who were contracted by an international consumer packaged goods company. Reports indicate that attackers gained access by calling service desks and convincing the employee to reset an account password on their behalf. Once the group gained access, they deployed malware in the manner of a ransomware attack, causing major disruptions in the production and distribution of the company’s goods. The scale of the damage was outlined in a lawsuit filed by the company against the IT service provider, which sought €326 million in damages.
While this attack example dates to 2023, Scattered Spider continues to be active. In June 2025, the group reportedly targeted American businesses in a similar manner. Some alleged members of the group were arrested in the aftermath of the recent attacks.
Notwithstanding the arrests, the apparent effectiveness of Scattered Spider’s attacks is one reason why we believe that operational controls such as out-of-band authentication could become a topic of renewed interest. No company wants to be defrauded, but reports of attacks that cause major disruption to core business operations have a way of attracting board-level attention, and spurring action. If threat actors continue to use social engineering and BEC tactics as a prelude to encryption, data theft and extortion, it’s likely that businesses will focus on the controls that can prevent individuals from being tricked.
Accounts compromised: Not just email
Business Email Compromise is so named because the compromise is typically an email account – but it is not always. In our last quarterly report, we discussed examples in which threat actors had compromised business collaboration platforms to perform BEC-like social engineering exploits. In Q2 2025, we continued to see this trend progress with more examples, so it bears mentioning again in any discussion of BEC.
These tools make a tempting target for misuse because they have become a common and expected method of internal communications within customer environments. Most employees have been trained to look out for suspicious emails, but since collaboration tools are typically restricted to individuals directly employed by the organisation, many would rarely think twice about a message sent on the platform. This approach has led to both BEC claims as well as the initial vector for broader ransomware attack campaigns. Once the account takeover takes place, threat actors easily pivot to shared online repositories scanning for sensitive (PII/PHI) and proprietary data (customer info, blueprints, engineering documents, etc.).
Defending against BEC: Controls, remediation and the role of Out-of-Band Authentication
Since BEC relies more on procedural gaps and human error than malware or software exploits, defense requires a combination of technical safeguards and strict operational discipline. One of the most effective controls is Out-of-Band Authentication (OOBA) – verifying sensitive requests like payment changes or updates to contact information via an independent communication channel.
Organisations should never rely solely on email for confirming high-risk actions. Effective controls include:
- Verifying requests using a known phone number, not one provided in the message.
- Initiating a test transaction to confirm new banking details before updating records.
- Reenforcing that procedures must always be followed, no exceptions – even (and particularly) if the request is made with a high degree of urgency.
OOBA should be more than a guideline – it must be a formal requirement, embedded into financial operations and reinforced through regular training. Organisations should retrain staff handling payments at least yearly and should revisit possible procedure changes after experiencing leadership changes, system upgrades or periods of increased phishing activity.
On the technical front, layered defences remain essential, and include:
- Multifactor Authentication (MFA) for all access to email and financial systems, ideally using phishing-resistant methods (e.g., hardware tokens or app-based authenticators).
- Email authentication protocols (SPF, DKIM, DMARC) to reduce spoofing.
- Behavioural anomaly detection to flag suspicious login activity or deviations in financial behaviour.
Regular employee training in procedures like those outlined above remains the cornerstone of BEC defence. Recent studies have shown that, while phishing training does make an impact, especially when it’s been conducted recently, there may be a ceiling to its effects. In other words, no amount of additional training is likely to reduce any organisation’s risk of a social engineering exploit to zero. That means organisations need to look to the next layer down – how employees respond in the face of certain types of requests, even from fellow employees – to add layers of defence.
Conclusion
In the second quarter of 2025 ransomware activity fell from Q1’s elevated level, though the level of activity continues to follow the general upward trendline that Travelers has observed over the past four years. Meanwhile, business email compromise and social engineering remain consistent, costly threats: in some cases, they are now being combined with extortion tactics. The persistence and evolution of these attacks only further reinforces the need for strong procedural controls and a layered approach to defence.
Recommendations from the Travelers Cyber Risk services team
To mitigate these cybersecurity risks, businesses should adopt security investments with the greatest return such as:
- Implement phishing-resistant MFA for all remote access and email.
- Run an effective vulnerability management programme to quickly patch critical vulnerabilities in edge devices, such as VPNs.
- Ensure you have reliable backups and have a resilient disaster recovery and business continuity plan.
- Run endpoint detection and response (EDR) solutions with 24x7 active monitoring.
These steps, together with cyber insurance that offers pre and post cyber breach services, can help a business better anticipate, withstand, and recover from a cyber event.
The information provided is for general informational purposes only. It does not, and it is not intended to, provide legal, technical, or other professional advice, nor does it amend, or otherwise affect, the provisions or coverages of any insurance policy issued by Travelers. Travelers does not warrant that adherence to, or compliance with, any recommendations, best practices, checklists, or guidelines will result in a particular outcome. Furthermore, laws, regulations, standards, guidance and codes may change from time to time, and you should always refer to the most current requirements and take specific advice when dealing with specific situations. In no event will Travelers be liable in tort, contract or otherwise to anyone who has access to or uses this information.
Travelers operates through several underwriting entities in the UK and Europe. Please consult your policy documentation or visit the websites below for full information.



